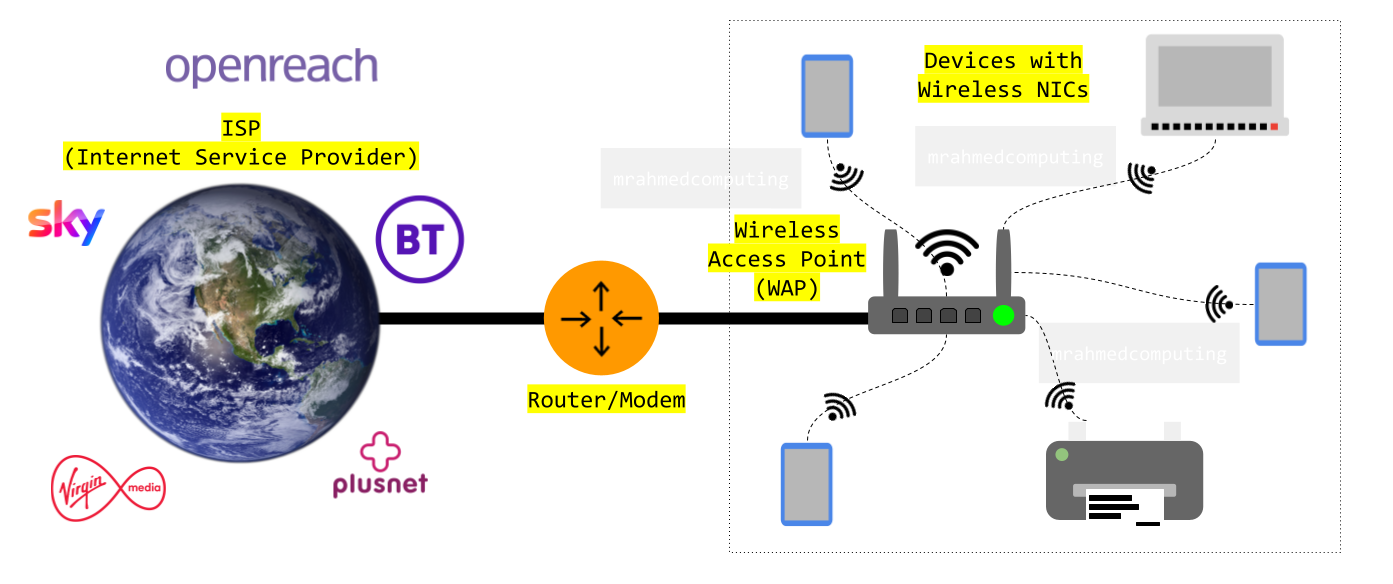
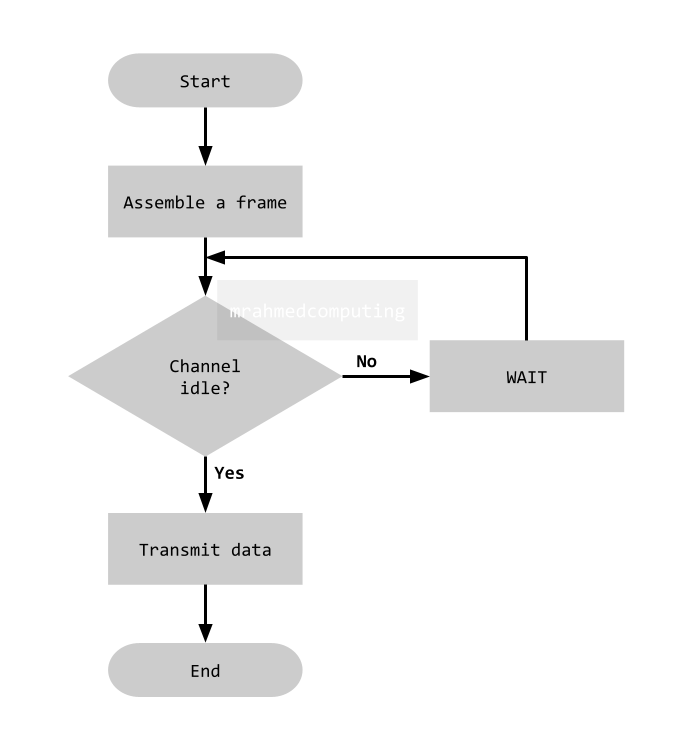
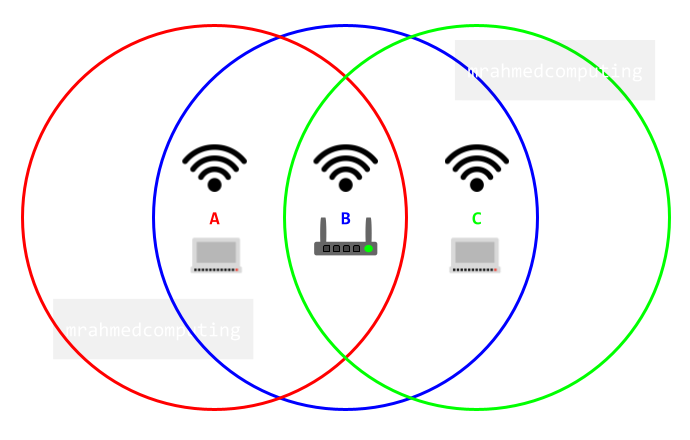
CSMA/CA
The described protocol aims to prevent collisions on a data channel. However, due to the issue of “hidden nodes,” it cannot always achieve collision avoidance. Instead, it relies on acknowledgments to confirm successful data arrival.
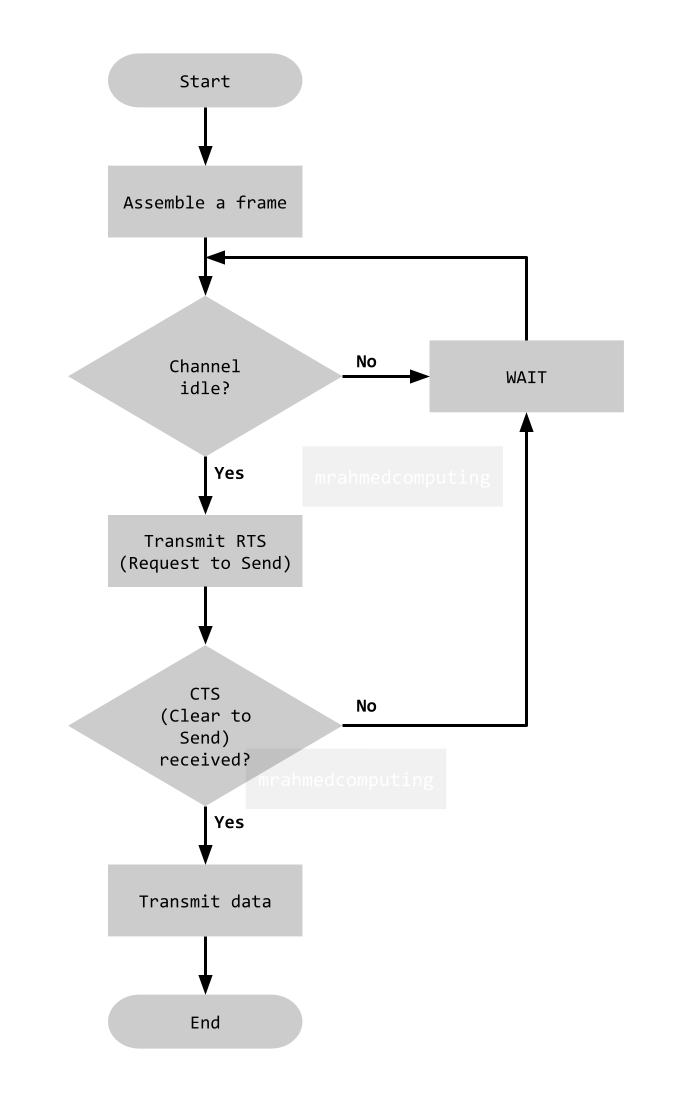
Before transmitting, a node listens for signals on the wireless network to check if another node is currently transmitting. If a signal is detected, the node waits for a random period before checking again.
Despite these efforts, data collisions can still occur. For instance, two nodes might transmit simultaneously when they both sense an idle channel. In such cases, the receiver won't send an acknowledgment back to the sender.
To address this challenge, the protocol employs a mechanism called RTS/CTS (Request to Send/Clear to Send) to overcome both the hidden nodes problem and collision issues.