Lesson Objectives
- Standards
- Protocols
- Be familiar with FTP, HTTP,HTTPS, POP3, SMTP, SSH.
- Understand FTP client software and servers.
- Understand how emails are sent and received.
- TCP/IP
KS3, GCSE, A-Level Computing Resources
A network standard is set of agreed requirements for hardware and software. Standards are important as they allow manufacturers to create products and programs that will be compatible with products and programs from other manufacturers.
Why are they important:
Standards serve as the fundamental building blocks for product development. They establish consistent protocols that can be universally understood and adopted. By adhering to these standards, manufacturers ensure that their devices can seamlessly communicate with other compatible devices. For instance, your smartphone connects automatically to your home Wi-Fi network because of these standards, ensuring your maps and playlists stay up to date without any manual intervention.
Design standards simplify the development process. When creating new products, manufacturers don't have to start from scratch. Instead, they follow established norms, saving time and effort. These standards provide detailed guidelines on how devices identify each other, how data flows between them, and how security is maintained. This streamlines product development and speeds up time-to-market.
Globally adopted standards facilitate international trade. When manufacturers follow consistent protocols, it becomes easier to export and import products across borders.
A protocol is a set of rules that allow computers to communicate over a network.
Why are they important:
Protocols serve as standardized sets of rules for formatting and processing data. Computers within a network may use diverse software and hardware, but adherence to protocols enables them to communicate effectively.
By following protocols, devices ensure consistency and interoperability. When two computers both use the Internet Protocol (IP), they can communicate seamlessly. However, if one uses IP and the other doesn't, communication breaks down.
HTTP (Hypertext Transfer Protocol) is used for accessing and receiving web pages in the form of HTML files on the Internet.
HTTPS (Hypertext Transfer Protocol Secure) is an extension of HTTP that works to protect communication between web servers and browsers when transporting data.
The key difference between these protocols lie in security. HTTP sends data in plain text, making it vulnerable to interception and tampering. HTTPS, on the other hand, secures connections using a digital security protocol that encrypts and validates data.
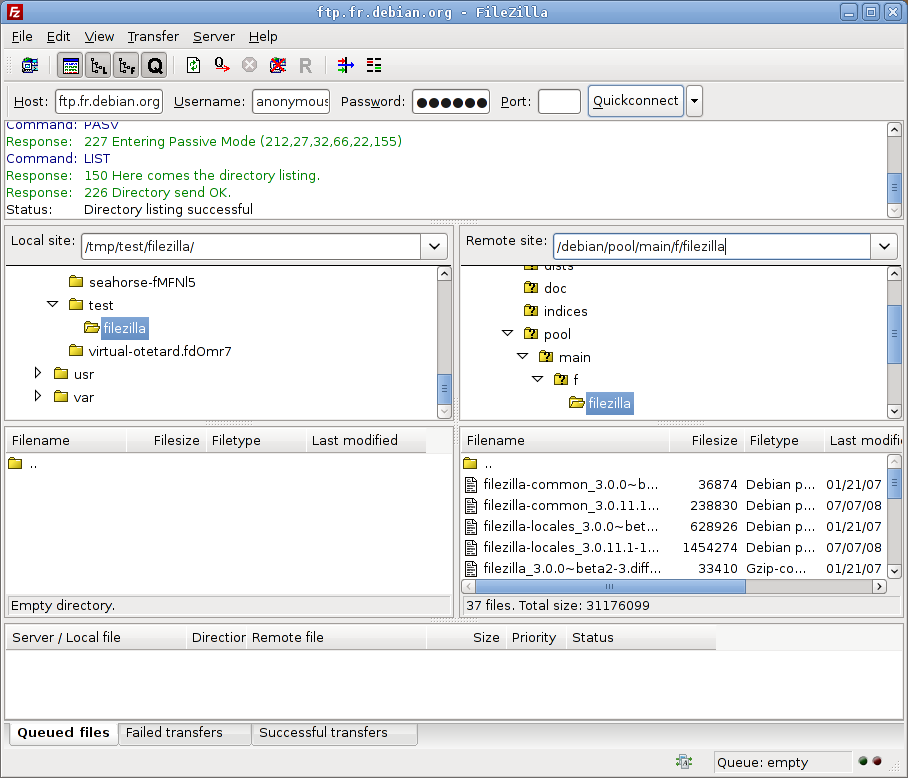
(File Transfer Protocol) is a standard network protocol used for transferring files between computers over a TCP-based network, such as the Internet. FTP operates on a client-server architecture. FTP users can authenticate themselves using a plain-text sign-in protocol (usually a username and password).
File Transfer Protocol is an application level protocol used to move files across a network. FTP uses the client-server model with separate data and control channels operating on ports 20 and 21.
Usernames and passwords are frequently used to protect access to files and to identify users. However, access can also be provided anonymously where any user can access the FTP site without the need to log in.
A port serves as a virtual endpoint where network connections start and end. These software-based ports are managed by a computer's operating system. Each port is associated with a specific protocol. By using different ports, computers can easily distinguish between various types of traffic. For example, emails and webpages may arrive over the same Internet connection, but they are directed to different ports for efficient handling.
You can get more information from: https://www.cloudflare.com/en-gb/learning/network-layer/what-is-a-computer-port/
Here are several common application level protocols and their standard port numbers:
| Port Number | Protocol |
|---|---|
| 20 | File Transfer Protocol (FTP) DATA |
| 21 | File Transfer Protocol (FTP) CONTROL |
| 22 | Secure Shell (SSH) Remote login |
| 23 | Telnet (unencrypted) Remote login |
| 25 | Simple Mail Transfer Protocol (SMTP) |
| 80 and 8080 | HyperText Transfer Protocol (HTTP) |
| 110 | Post Office Protocol v3 (POP3) |
| 143 | Interim Mail Access Protocol (IMAP) |
| 443 | HyperText Transfer Protocol Secure (HTTPS) |
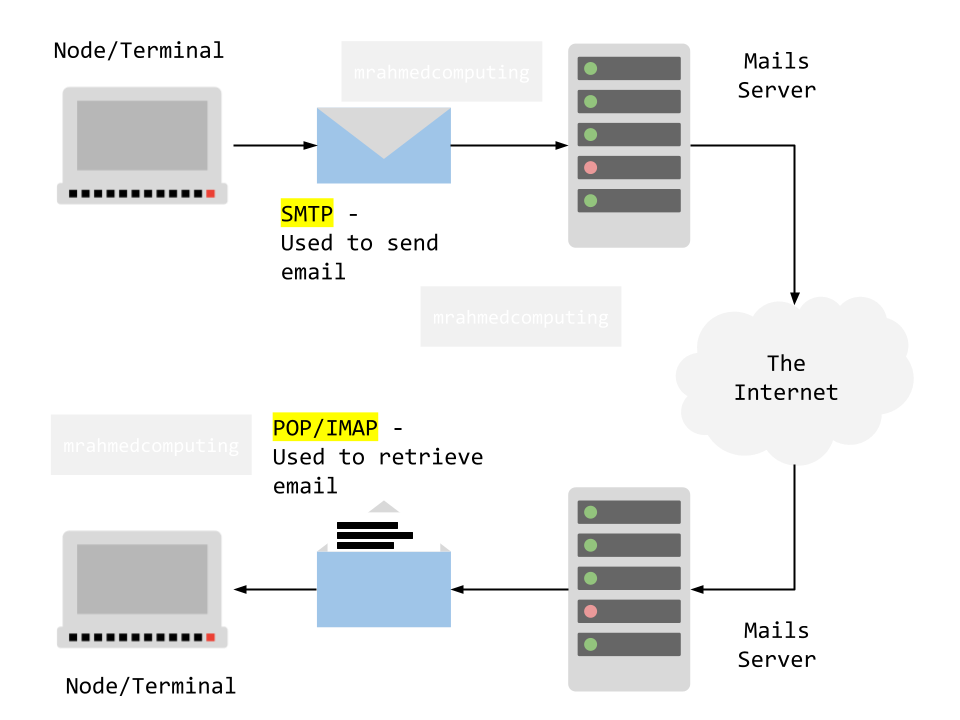
SMTP (Simple Mail Transfer Protocol): SMTP is responsible for sending emails from a client (like your email app) to a mail server. When you compose an email and click "send", SMTP handles the delivery process. It communicates with the recipient's mail server to relay the message.
IMAP (Internet Message Access Protocol): IMAP is an incoming mail protocol that allows you to access your email stored on a mail server. It keeps your email synchronized across multiple devices (phone, computer, tablet). IMAP downloads only email headers initially, improving efficiency. When you open an email, IMAP fetches the full content from the server.
POP (Post Office Protocol): It downloads entire emails from the server to your local device. Once downloaded, emails are removed from the server. POP is useful if you want to keep a local backup of your inbox. However, it's less suitable for managing emails across multiple devices.
TCP/IP (Transmission Control Protocol/Internet Protocol) is a fundamental framework for organizing communication protocols used on the Internet and similar computer networks.
TCP is one of the main protocols in the Internet protocol suite. It originated alongside the Internet Protocol (IP) during the early days of network implementation. Together, TCP and IP form the foundation of the suite, commonly referred to as TCP/IP. TCP ensures reliable, ordered, and error-checked delivery of a stream of data (octets or bytes) between applications running on hosts connected via an IP network.
IP handles addressing and routing of data packets across networks. It ensures that data reaches the correct destination based on IP addresses. IP is connectionless and operates independently of TCP.
The TCP/IP Stack, also known as the Internet Protocol Suite, is a fundamental framework for organizing communication protocols used on the Internet and similar computer networks.
The protocol stack defines four layers in which different protocols operate to pass data packets across a network. The four layers are divisions of network functionality, each carrying out different roles:
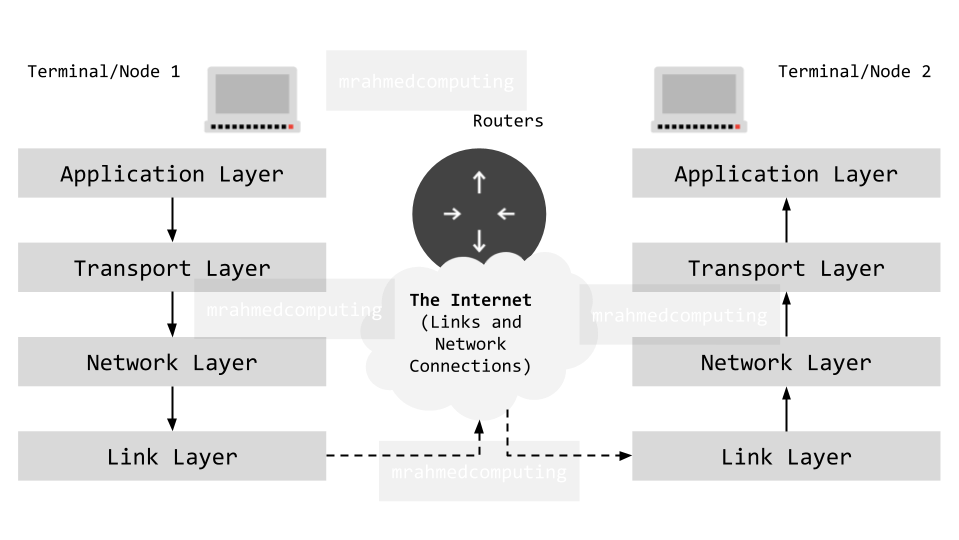
In summary, the TCP/IP model provides a structured way to understand how data flows across networks, from applications down to the physical hardware.
The application you are using to send data will determine the correct protocol to use to communicate.
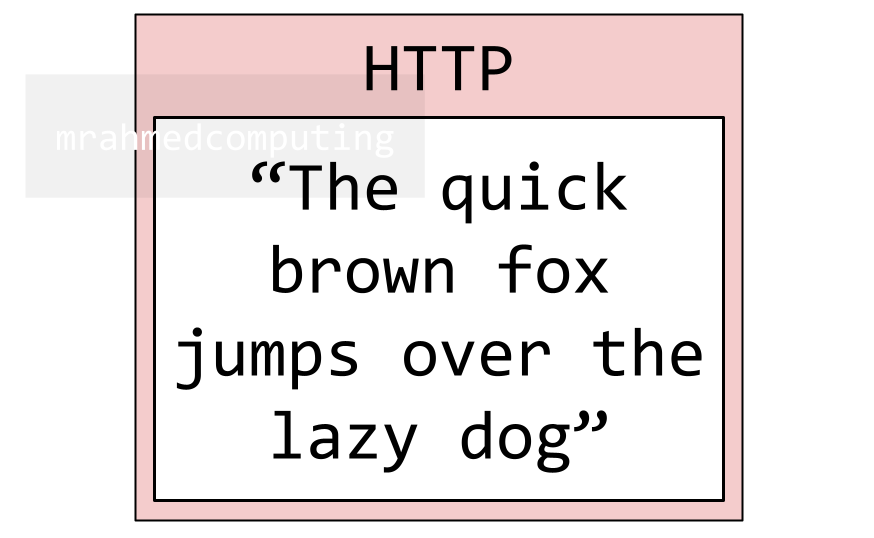
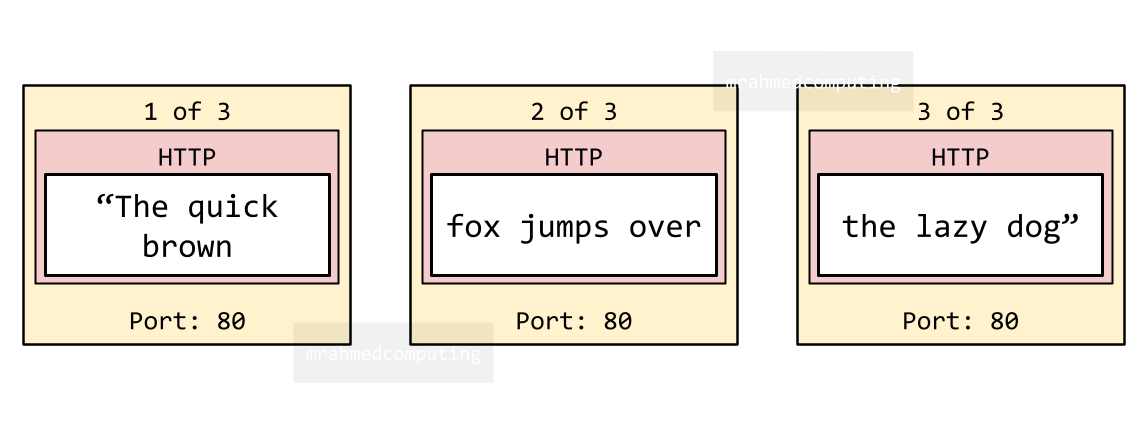
A web page is requested by a client computer.
As part of the web page, the following message is to be requested from a web server by the client browser using the HTTP protocol:
“The quick brown fox jumps over the lazy dog”
Application layer protocols serve as essential components for applications that need to communicate across a network, particularly over the Internet. These protocols operate at a high level and establish agreed-upon standards between the communicating endpoints.
These protocols do not dictate how data is physically transmitted; instead, they define the rules and conventions for what should be sent during communication.
Uses the Transmission Control Protocol (TCP) to establish an end-to-end connection with the recipient computer.
At the receiving end this layer confirms that packets have been received and requests any missing packets be resent.
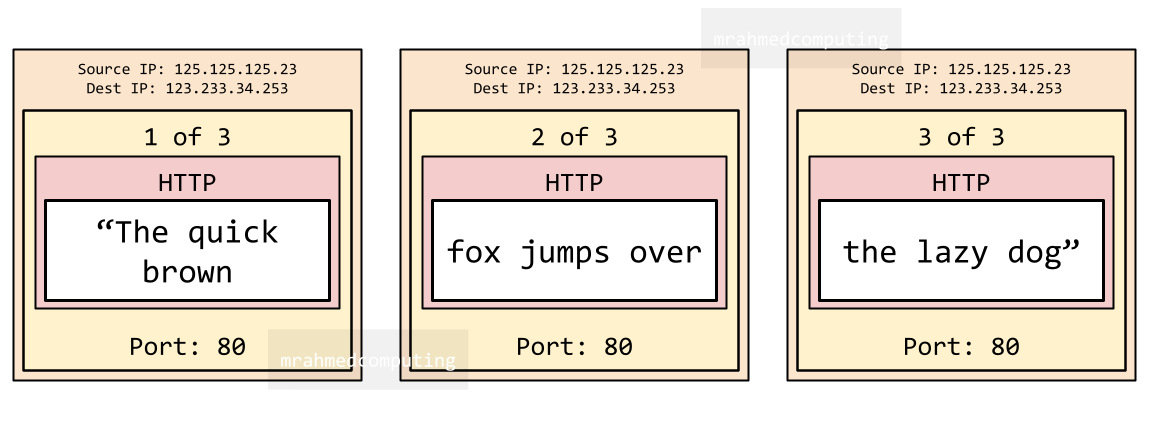
Packet routing relies on the Internet Protocol (IP) to address packets using source and destination IP addresses. Routing tables play a crucial role in this process.
When a router receives a packet, it determines the appropriate path based on the destination IP address. Each packet is forwarded toward an endpoint known as a socket, which is defined by the combination of an IP address and a specific port number. For example, the socket “125.125.125.23:80” corresponds to port 80 on the IP address 125.125.125.23.
A socket is composed of two essential components:
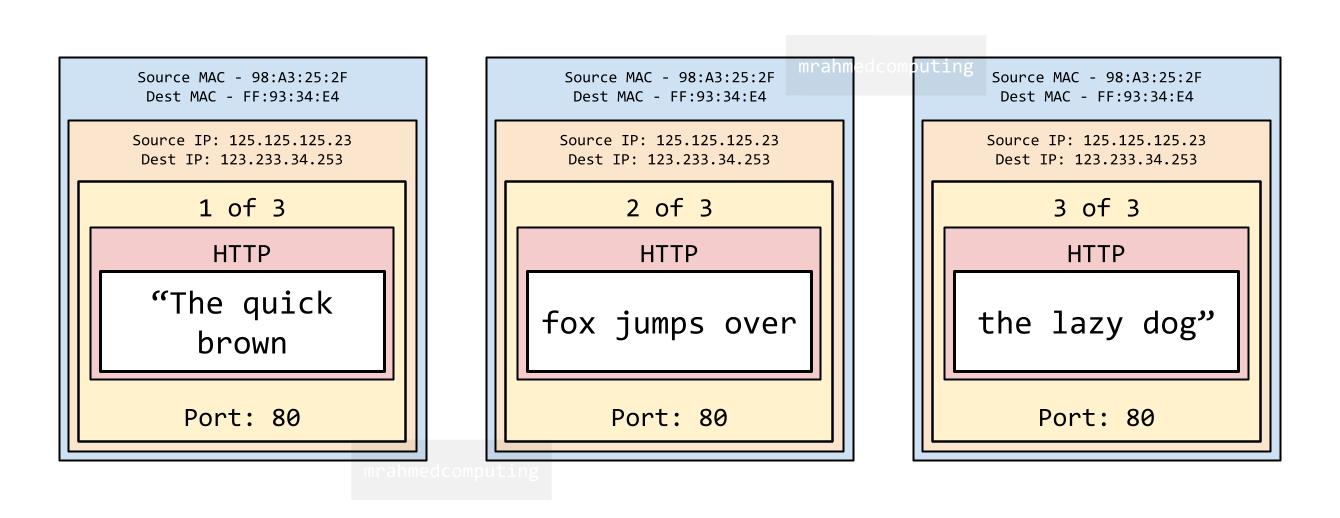
The link layer operates at the physical connection level.
It adds the MAC address (Media Access Control address) of the source and destination devices to each packet. These MAC addresses change with each hop as data traverses through different network devices.
Data packets move back up the layers to their destination application:
195.246.108.227
4B:24:A2:73:0E:F1
A layer is defined as a division of network functionality.
UDP (User Datagram Protocol) maintains an open data connection to send a continuous stream of packets without verifying if they are received correctly. It's most useful in scenarios where waiting to fill in gaps caused by lost packets doesn't make sense.