Lesson 5. Internet Security
Lesson Objective
- Understand how a firewall works.
- Explain symmetric and asymmetric encryption and key exchange.
- Explain how digital certificates and digital signatures are obtained and used.
- Discuss worms, trojans and viruses, and the vulnerabilities they exploit.
- Discuss how improved code quality, monitoring and protection can be used to address worms, trojans and viruses.
Lesson Notes
Part 1 of 6: Firewalls
A firewall describes the technique used to protect an organisation's network from unauthorised access by users outside the network.
A firewall can be constructed using hardware, software or a combination of both.
The most secure firewalls:
- Tend to be those constructed from both hardware and software.
- Checks outgoing and incoming traffic.
- Stops suspicious packets passing through.
- Blocking certain IP addresses.
Firewalls - Static Packet Filtering
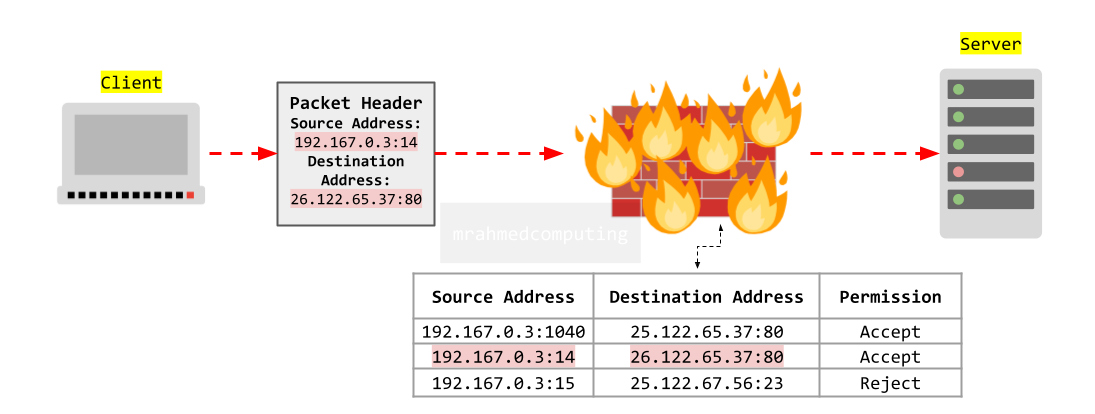
The firewall is a critical component in network security. It regulates network access based on predefined rules and policies.
Firewalls inspect the source and destination IP addresses in packet headers. If these IP addresses match those recorded on the administrator's “permitted” list, the packets are either accepted or allowed to proceed.
Certain protocols operate on specific ports. For instance, Telnet uses port 23. If Telnet is disallowed (due to security concerns), any packets attempting to connect through port 23 will face two outcomes:
- Dropped Packets: These are quietly removed without further notice.
- Rejected Packets: A rejection notice is sent back to the sender, indicating that the connection is not allowed.
Firewalls - Stateful Inspection (Dynamic Filtering)
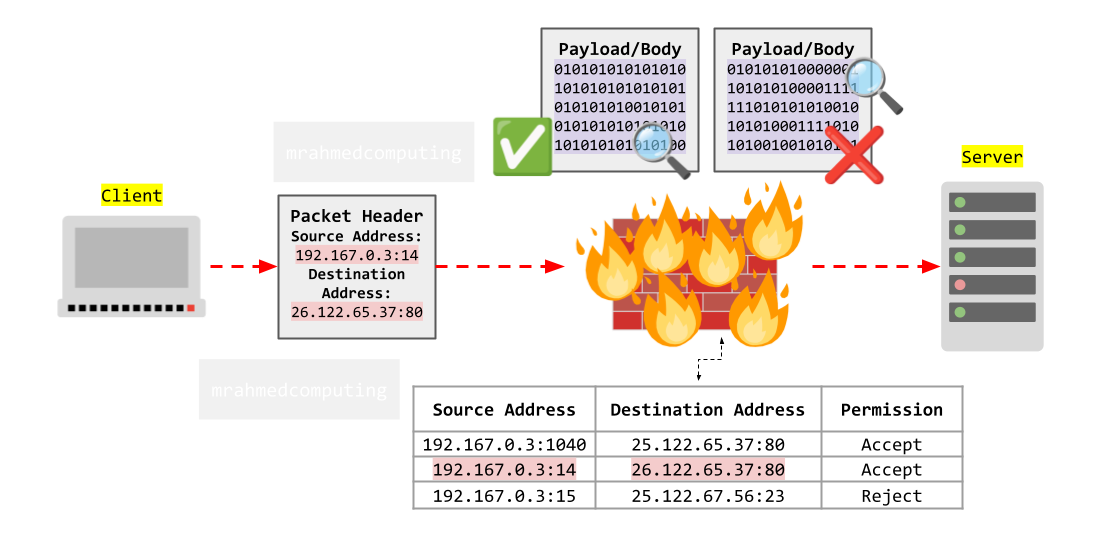
Instead of solely relying on IP addresses, protocols, and port numbers to manage a packet's safe traversal, stateful inspection (also known as dynamic filtering) examines the payload contents of data packets. This approach allows for a more thorough assessment of safety.
Rather than just examining the header information; stateful inspection analyzes the actual data within the packet. By inspecting the payload, it can identify potential threats or anomalies that might not be evident from IP addresses or port numbers alone.
Stateful inspection creates temporary contextual rules based on the history of previous packets in a communication "conversation". For example, if a series of packets indicates an ongoing legitimate exchange (such as a web request and response), the firewall dynamically adjusts its rules to allow further related packets.
Routers and firewalls maintain a connection table (also called a state table or session table). This table dynamically records information about active connections, including source and destination IP addresses, port numbers, and the state of the connection (e.g., established, closed, or waiting). The connection table is continuously updated as packets flow through the network. Administrators create rules that reference this table, allowing the firewall to make informed decisions based on the ongoing context of network conversations.
Firewalls - Proxy Server
A proxy server intercepts all packets entering and leaving a network, hiding the true network addresses of the source from the recipient. This enables privacy and anonymous surfing.
A proxy can also maintain a cache of websites commonly visited and return the web page data to the user immediately without the need to reconnect to the Internet and re-request the page from the website server. This speeds up user access to web page data and reduces web traffic.
Proxy servers are often used to filter requests made by users. A common example is a school web-proxy that filters unsafe online content.
By routing through a proxy server there is no direct connection between the computer on the LAN and the Internet.

Part 2 of 6: Encryption
Encryption is the use of an algorithm and a key to convert message data into a form that is unreadable without the key to decrypt the data.
- Used to secure information during transmission so that only the sender and receiver can understand the message.
Decryption is the use of an algorithm and a key to convert encrypted message data into plain text.
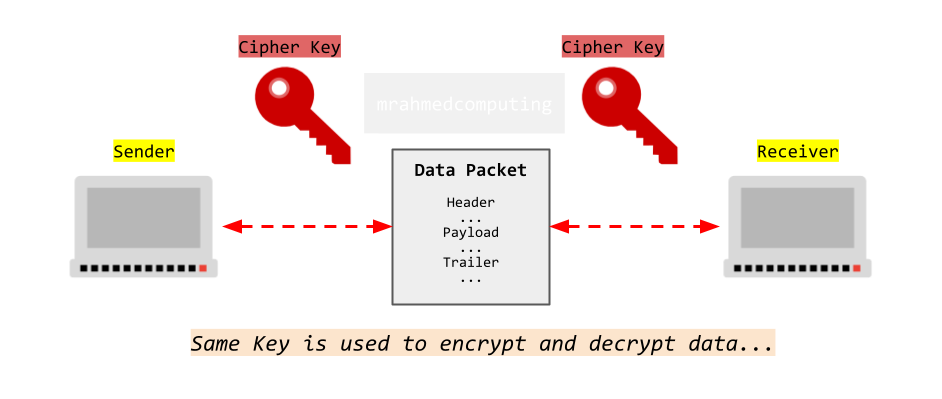
Symmetric Encryption (Private Key)
Symmetric encryption is any technique where the same key is used to both encrypt and decrypt the data. The Caesar Cipher is one of the simplest symmetric encryption techniques, and of course, one of the easiest to crack.
Here are some symmetric encryption methods:
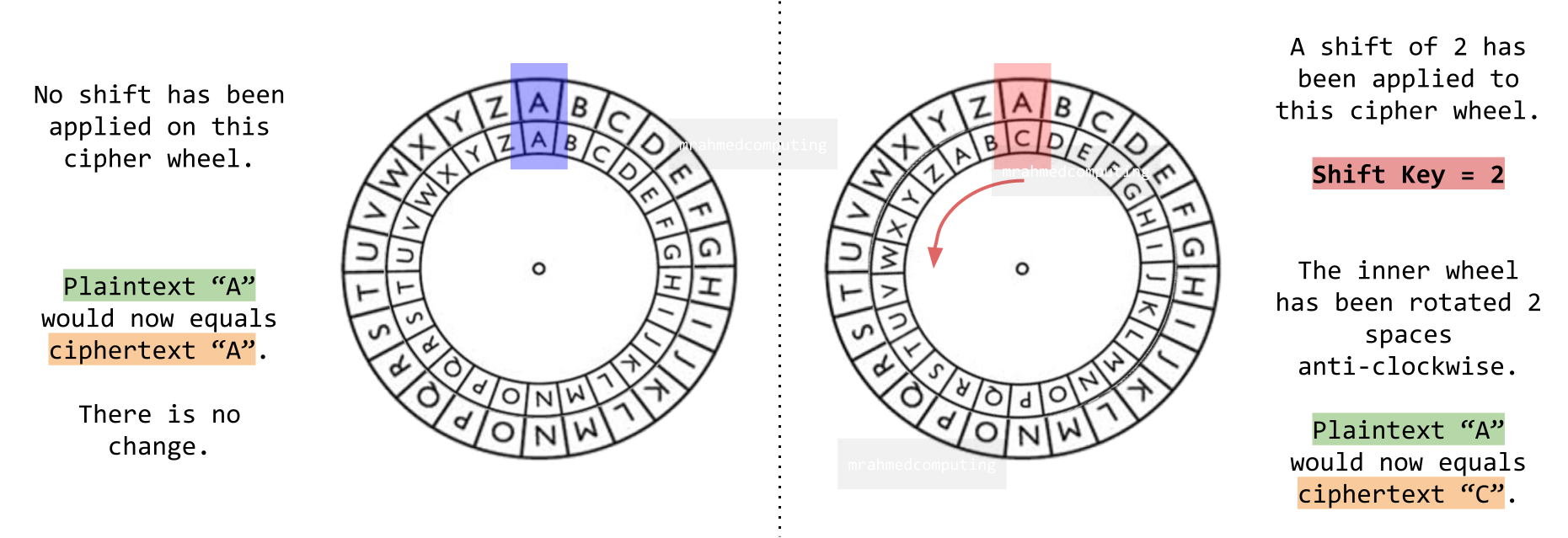
Caesar Cipher
The Caesar cipher is a substitution cipher where each letter in the plaintext is replaced by a letter a fixed number of positions down the alphabet. It is named after Julius Caesar, who used it in his private correspondence.
How does it work?
Choose a shift value (usually between 1 and 25). Shift each letter of the alphabet by the chosen value. For example, with a left shift of 3, 'D' becomes 'A', 'E' becomes 'B', and so on. Now look at the example below:
- Plain: “THE QUICK BROWN FOX JUMPS OVER THE LAZY DOG”
- Ciphertext (with a left shift of 3): “QEB NRFZH YOLTK CLU GRJMP LSBO QEB IXWV ALD”
To decrypt, perform a right shift by the same value.
Here is another example. Can you work out the cipher key?
Plain: ABCDEFGHIJKLMNOPQRSTUVWXYZ
Cipher: FGHIJKLMNOPQRSTUVWXYZABCDE
RJJY RJ FY YMJ TQI GFWS
“MEET ME AT THE OLD BARN”
Here is a diagram of a Caesar Cipher wheel.
Vernam Cipher
The Vernam Cipher, also known as the “One-Time Pad”, is a powerful and unbreakable encryption technique when used correctly.
The Vernam Cipher falls under the category of symmetric encryption. Both the sender and recipient share the same secret key.
The Vernam Cipher uses a random or pseudorandom stream of data (the keystream). Each character of the plaintext is combined with the corresponding character from the keystream using the Boolean “exclusive or” (XOR) function. The resulting ciphertext is generated.
When used with a truly random and secret key of the same length as the plaintext, the Vernam Cipher is unbreakable. It provides exceptional security because the keystream is unpredictable and used only once (hence the term “one-time pad”).
Example:
Cat = 01000011 01100001 01110100
pop = 01110000 01101111 01110000
You then perform an XOR operation (like binary addition) using the keyword.
Ciphertext = 00111111 00001110 00000100
Ciphertext = 63, 14, 4 (Denary)
Ciphertext = 3F, 0E, 04 (Hex)
Extra:
The Vernam Cipher was devised in 1918 by Gilbert S. Vernam, an engineer at AT&T. It introduced a crucial improvement to the Vigenère cipher, attributed to the 16th-century French cryptographer Blaise de Vigenère.

| A |
B |
Z |
| 0 |
0 |
0 |
| 0 |
1 |
1 |
| 1 |
0 |
1 |
| 1 |
1 |
0 |
Cryptanalysis
Cryptanalysis involves attempting to “break” a cryptographic code without having knowledge of the specific cipher or the secret key. While symmetric encryption relies on a shared secret key between the sender and receiver, modern computers can easily compromise it. Despite efforts to keep the key secret, the vulnerability remains.
Exmaple Technique: Brute Force Attack
A brute force attack is an attempt to crack a password using a trial and error approach and hoping, to guess it correctly. This is a dated attack method, but is still effective and commonly used by hackers. Depending on the strength of a password, cracking it can take anywhere from a few seconds to many years.
Asymmetric Encryption (Public Key)
Asymmetric encryption is a technique which uses different keys for encryption and decryption, allowing computers over the Internet to securely communicate with each other. Here are a list of steps outlining the public key encryption process:
- Key generation: Each person (or their computer) must generate a pair of keys that identifies them: a private key and a public key. The sender's public key and private key are mathematically related, and the receiver's public and private keys are mathematically related. The current nationally recommended key length is 2048, or even 3072 bits.
- Key exchange: The sending and receiving computers exchange public keys with each other via a reliable channel, like TCP/IP. The private keys are never exchanged.
- Encryption: The sending computer encrypts the secret data using the receiving computer's public key and a mathematical operation. The power of public key encryption is in that mathematical operation. It's a "one-way function", which means it's incredibly difficult for a computer to reverse the operation and discover the original data. Even the public key cannot be used to decrypt the data. The math of the one-way function relies on prime numbers, the difficulty of factoring large primes, and modular arithmetic.
- Sending encrypted data: The sender can now safely transmit the encrypted data over the Internet without worry of third parties.
- Decryption: Now the receiver can decrypt the message, using their private key. The only key that can be used to decrypt the message (in the world!).
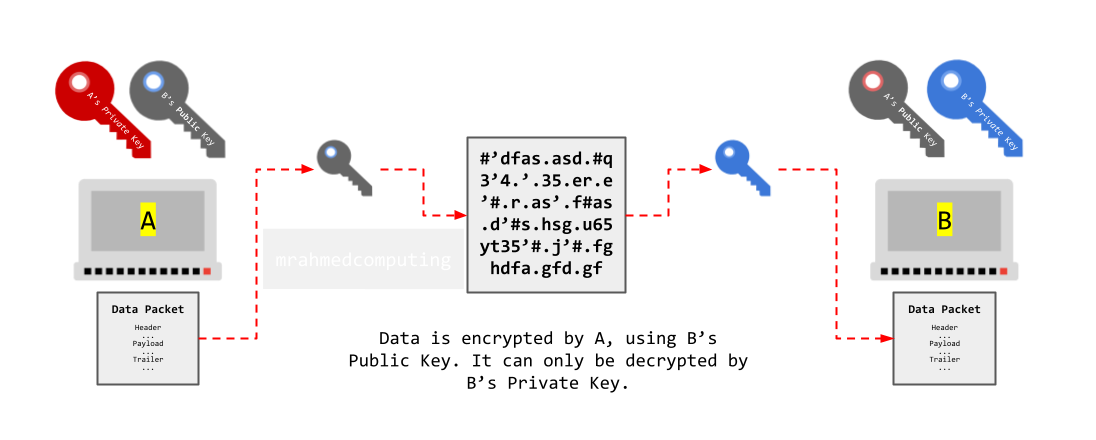
Example - Computers A and B:
- A will only have a private key known only to A.
- A will also have a public key, which is mathematically related to A's private key. It is called a public key because anyone can access it.
- B will also have a private key and a related public key.
- For A to send a secure message to B, A will first encrypt the message using B's public key.
- As the public and private keys are related, the message can only be decrypted by B using B's private key.
- As no-one else knows B's private key, even if the message was intercepted, it could not be decrypted.
Genuine Communication?
While encryption typically involves using the recipient's public key to secure a message, a malicious third party could encrypt a message using your own public key. This deceptive approach might lead you to believe that the message is legitimate, but in reality, it could be from an unauthorized source.
Digital Certificates
Digital certificates serve as trusted credentials issued by certification authorities (CAs). These certificates verify the association between a public key and its owner. When you receive a public key, a valid digital certificate enhances confidence in its authenticity.

Digital Signatures
To ensure the authenticity and integrity of an electronic message, a sender can digitally sign it. Digital signatures use the sender's private key to create a unique cryptographic hash of the message. Recipients can verify this signature using the sender's public key.
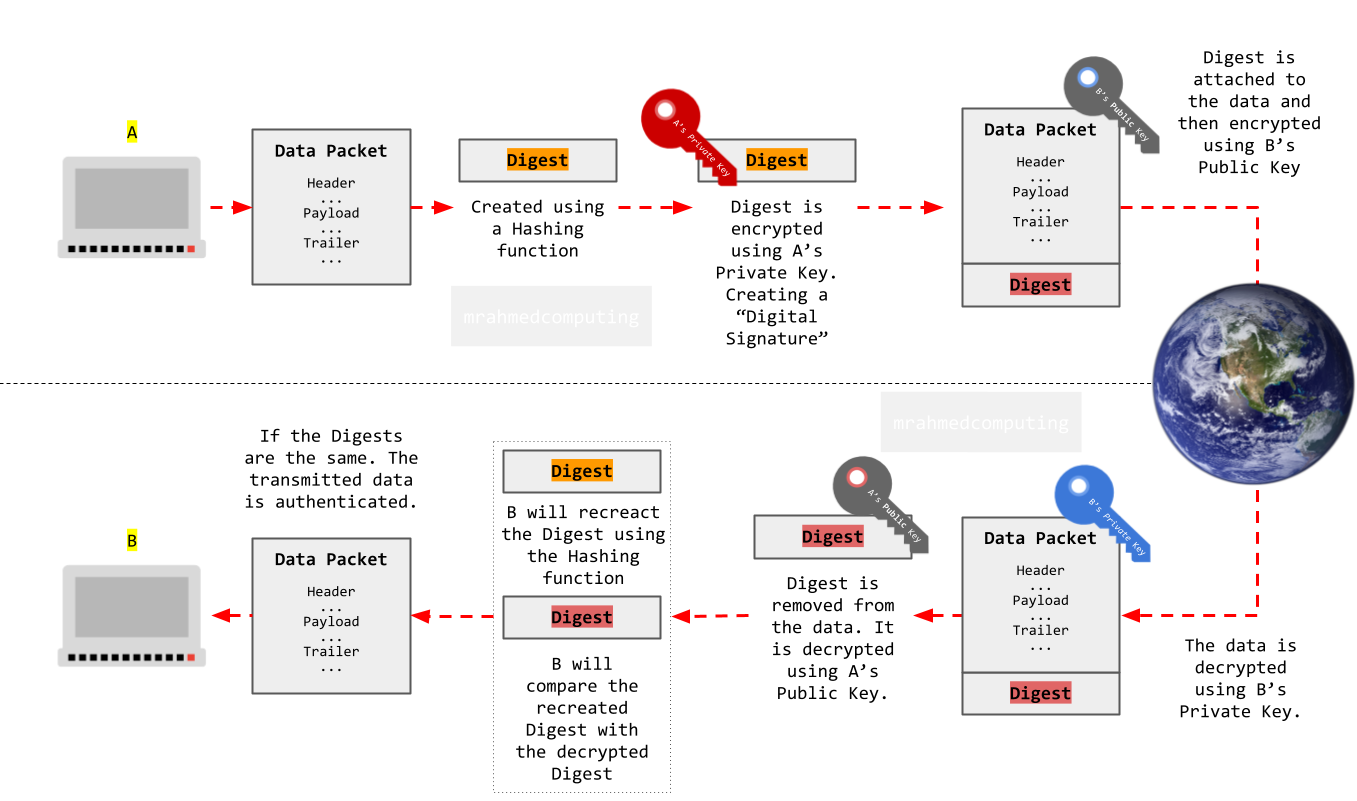
Hashing ##########
A hashing function is a way to turn any length input into a unique fixed length code. This code is called a hash.
It is very difficult to turn a hash back (almost impossible - one way encryption) into the original input, so hashing is often used to protect sensitive data, such as passwords.
Here is an example:
Input: “mypassword”
Hash: “1234567890abcdef1234567890abcdef”
Input: “myPassword”
Hash: “fedcba0987654321fedcba0987654321”
To store a password securely, a website or app will hash the password before storing it in its database.
When you try to log in, the website or app will hash your password again and compare it to the stored hash. If the two hashes match, then you are allowed to log in.
If a hacker steals a password database, they will only see the hashes, not the actual passwords. Hashing is a very important security measure for protecting passwords and other sensitive data.
Popular methods:
Part 3 of 6: Network Security
Ensuring the security of data on a network is crucial. When networks are compromised, it can lead to various negative consequences:
- Financial Loss: Breaches can result in financial damages, including theft of funds or costly recovery efforts.
- Reputation Damage: A hacked network tarnishes an organization's reputation. Trust from customers, partners, and stakeholders may erode.
- Public Image Issues: News of a security breach spreads quickly. Public perception of the affected entity can suffer.
- Intellectual Property (IP) Theft: Stolen IP, trade secrets, or proprietary information can harm a company's competitive edge.
1. Authentication
Authentication is the process that verifies the identities of individuals, applications, or services before granting them access to digital systems and resources.
Why is authentication important?
- Protecting Systems: Authentication safeguards systems, data, networks, websites, and applications from unauthorized access.
- Individual Privacy: Strong authentication empowers individuals to conduct online business (e.g., banking) with less risk.
2. Encryption
Encryption is the process of scrambling data so that it can not be understood by individuals without appropriate access rights.
Encryption takes plain text (like a text message or email) and scrambles it into unreadable format called ciphertext. This process ensures that even if hackers or cybercriminals intercept the data, they can't read it. The intended recipient, equipped with a decryption key, can unscramble the information back into plain, readable text.
You should encrypt messages, files, and data containing personal, sensitive, or classified information.

3. Firewall
A firewall is like a protective barrier for a network. It allows outgoing traffic but carefully examines incoming traffic. Suspicious packets are blocked, and improper content is rejected. Firewalls also filter unwanted inbound traffic, including blocking specific IP addresses.
4. MAC Address Filtering
MAC address filtering is a network security feature that controls access to a wireless network based on the unique MAC addresses of devices.
Whitelisting (Allowlisting):
- Whitelisting is a security approach that allows only specific, pre-approved items while blocking everything else. This is a very secure choice, however managing and updating the whitelist can be difficult.
Blacklisting (Denylisting):
- Blacklisting is the opposite of Whitelisting and involves creating a list of MAC addresses that are not allowed to access the network. A blacklist can prevent traffic from known entities. As new threats emerge, the blacklist must be continuously updated.
5. Network Policies
Acceptable Use Policy (AUP):
An AUP is an agreement between parties within a computer network community. It outlines standards of behavior regarding the proper usage of specific hardware and software services. AUPs are crucial for minimizing legal risks and ensuring that users adhere to approved behavior.
Disaster Recovery Policy:
This policy prepares an organization for data loss due to disasters such as fire, flood, hardware failure, or hacking. It encompasses evaluating risks, implementing preventive actions, training staff, and executing post-disaster recovery tasks such as procuring replacement hardware, reinstalling software, and restoring data from backups.
Archiving Policy:
Archiving involves storing data no longer in frequent use for security, legal, or historical reasons. Policies define how long data should be retained and how to destroy or delete it after that time. Archiving frees up resources and allows faster access to active data.
Failover Policy:
Failover policies determine how network traffic is rerouted in case of adapter failure. It ensures redundancy by including multiple physical NICs in a team. Failover order specifies which NICs to use when an adapter fails.
Security Policy:
A security policy outlines rules and procedures for network access, authentication, authorization, and encryption. It covers areas like acceptable behavior, incident response, and data protection.
Part 4 of 6: Malware?
Malware, short for malicious software, refers to any intrusive software developed by cybercriminals (often called hackers) to steal data and damage or destroy computers and computer systems. Examples of common malware include viruses, worms, Trojan viruses, spyware, adware, and ransomware.
Here are some telltale signs that you might have malware on your system:
- Computer performance slows down significantly.
- Unexpected pop-up ads.
- Stolen, alterd or deleted data.
1. Viruses
A virus is a type of malware that attaches itself to legitimate programs or files. When these infected files are executed, the virus spreads and replicates, often causing damage to data or system files. Viruses can spread through infected email attachments, removable storage devices, or malicious websites.
2. Trojan Horse
Named after the ancient Greek story of the wooden horse used to infiltrate Troy, Trojans are deceptive programs. They appear harmless or useful but hide malicious code. Unlike viruses, Trojans don't self-replicate. Instead, they rely on user actions (such as downloading a fake app) to spread.
3. Spyware
Spyware is designed to secretly monitor a user's activities without their knowledge. It can track keystrokes, capture screenshots, record browsing history, and steal sensitive information like passwords or credit card details. Spyware often infiltrates systems through malicious downloads or compromised websites.
4. Adware
Adware is less harmful but annoying. It displays unwanted advertisements (pop-ups, banners, or redirects) to generate revenue for the attacker. While not as destructive as other malware, adware can slow down your system and disrupt your browsing experience.
5. Ransomware
Ransomware is particularly malicious. It encrypts your files or locks you out of your system, demanding a ransom (usually in cryptocurrency) to restore access The infamous WannaCry attack is an example of ransomware that affected thousands of computers worldwide.
6. Rootkit
A rootkit is a type of malicious software (malware) designed to gain unauthorized access to a computer system and maintain control over it while remaining hidden from the user or system administrators. A rootkit provides an attacker with a backdoor into an infected machine, granting them access to the computer.
Part 5 of 6: Detecting Vulnerabilities
Organizations may have vulnerabilities in the following areas
- Procedures: These include policies and codes of conduct.
- Operating System or Network Setup This pertains to how the operating system facilitates interactions with other parts of the network.
- Software Configurations It involves aspects like passwords and the accessibility of tools.
- Employee Behavior This refers to an employee's actions with their granted access and whether they can be trusted.
Method 1: Anti-Malware
Software that is used to detect and remove malware.

Method 2: Password Systems
Passwords are the most common form of authenticating a user. Authentication is checking that the user is allowed to access content. Some applications use a pin pattern instead of a username and password
To set a secure password you must
- Use a minimum of eight characters.
- Use a mixture of numbers, lowercase and uppercase characters.
- Include symbols such as &, !, #, %
- Do not include your name, DOB or personal details.
Example of strong password: Brdu8#Jw4g
Method 3: Biometric Authentication
Biometric security is a powerful mechanism that leverages unique biological measurements or physical characteristics to verify an individual's identity and grant access to a facility or system. Unlike traditional passwords, which can be vulnerable, biometrics link proof of identity to our bodies and behavior patterns. Examples of biometric technology include fingerprint mapping, facial recognition, and retina scans.
Method 4: Encryption
Encryption is the encoding of data so that it can no longer be easily understood. Only authorised users, or users with the key can decrypt it.
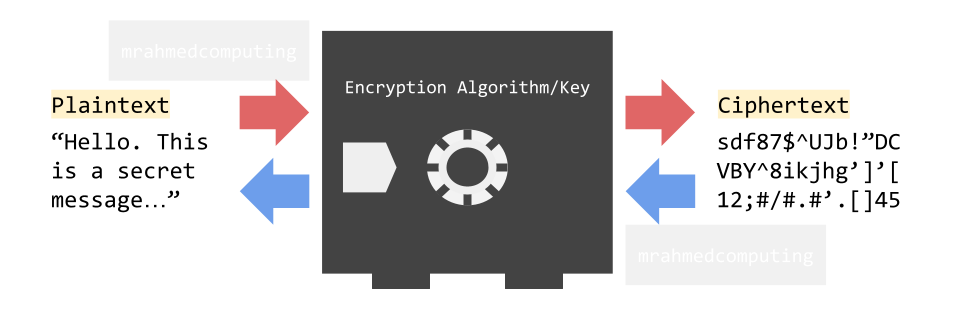
Method 5: CAPTCHA
CAPTCHA, an acronym for Completely Automated Public Turing test to tell Computers and Humans Apart, serves as a crucial security mechanism. Its purpose is to differentiate between human users and automated bots, particularly in scenarios like signing up for internet services.
Method 6: Email Confirmation
Email confirmation serves as a security measure in several ways:
- Account Verification: When you sign up for an online service or create an account, the platform typically sends a confirmation email to the address you provided. By clicking on the confirmation link in the email, you verify that you have access to that email account. This prevents unauthorized users from creating accounts using your email address.
- Preventing Fake Accounts: Confirmation emails ensure that only legitimate users can complete the account creation process. Without confirming their email, potential scammers or bots cannot fully activate their accounts.
- Two-Factor Authentication (2FA): Some services use email confirmation as part of a two-step verification process. After entering your password, you receive a code via email that you must enter to access your account. This adds an extra layer of security beyond just a password.
- Password Recovery: When you forget your password, many platforms allow you to reset it by sending a link to your registered email address. Confirming your email ensures that only authorized users can reset their passwords.
- Communication Channel: Email is a common communication channel for account-related notifications, security alerts, and password changes. Confirming your email ensures that you receive these critical messages.
Method 7: Automatic Software Updates/Patches
Large companies like Microsoft often automatically update your software whenever they make changes to it. During software installation, you can set the default option to install automatic updates. Free applications typically do not have automatic update capabilities, so manual updates may be necessary. Software patches are updates designed to improve or fix a program. It may also provide additional protection against malware.

Method 8: Penetration Testing
Finding flaws in a system, creating a report and explain how to fix them.
- In black box testing, testers are given no more information than any potential hacker may have.
- In white box testing, testers are given as much information as an 'insider' may have, in order to determine how much damage a rogue employee could do to a system.
Different types testers or hackers can have different motivations and they are categorized into the groups identified below:
- A white hat hacker is someone who has permission and is authorised to act as a penetration tester.
- A grey hat hacker is an individual who may not have explicit permission but conducts penetration testing and informs organizations about any vulnerabilities they discover-often in exchange for a fee. While grey hat hackers occasionally operate in a legal gray area, they are not inherently malicious.
- A black hat hacker is someone without permission and who has malicious intent. These are the people that penetration testers are trying to stop.
Method 9: Removable Media Ban
Cybercriminals occasionally employ a clever tactic! They strategically "lose" malware-infected USB sticks in places like company parking lots. Their goal is to trick unsuspecting employees into picking up these USB drives and plugging them into their computers. Thankfully, in some cases, vigilant employees have thwarted these attempts by reporting the suspicious devices to their IT departments. It's a reminder to stay cautious when encountering stray USB drives!
Method 10: Access Rights
Access rights in network security refer to the permissions and privileges granted to users, devices, or processes within a networked environment. These rights determine what actions an entity can perform and what resources it can access.
Method 11: Acceptable Use Policy (AUP)
Set of rules to follow in an organisation. If the rules are broken the organisation has legal grounds to remove you.

Method 12: Physical Security
Physical security is used to prevent physical access to devices, and to prevent theft. Steps may include:
- door locks
- window locks or bars
- intruder alarm systems
- CCTV systems
- laptop locks (e.g. Kensington locks)
- security guards.
Part 6 of 6: Protection - User, Admin, Programmer Levels
To protect yourself at the user level:
- Anti-Virus and Anti-Malware: Install and regularly update anti-virus and anti-malware software to detect and prevent malicious threats.
- Operating System Updates: Keep your operating system (OS) up to date with the latest security patches. These updates address vulnerabilities and enhance system security.
- Firewall Protection: Enable a firewall to filter incoming and outgoing network traffic. Firewalls act as barriers against unauthorized access.
- Attachments and Pop-Ups: Be cautious with email attachments and avoid clicking on pop-ups from unknown senders. Malicious attachments and pop-ups can harbor threats.
- Whitelisting Trusted Sites: Maintain a whitelist of trusted websites. Only visit sites that are known to be safe and secure.
- HTTPS, Digital Signatures, and Certificates: Ensure websites use HTTPS (secure communication) to protect data in transit. Verify digital signatures and certificates to validate the authenticity of websites and software.
- Strong Passwords: Use unique and strong passwords for programs, files, and online accounts. Consider using a password manager.
- Data Encryption: Encrypt sensitive data files to prevent unauthorized access. Encryption adds an extra layer of protection.
To protect a network at admin level:
- Source Verification: Verify that requests originate from recognized and authorized sources. Implement access controls to ensure only legitimate entities can interact with your network.
- Network Firewall: Deploy a network firewall to regulate incoming and outgoing traffic. Leverage packet filtering and stateful inspection techniques to scrutinize data packets, allowing or denying access based on predefined rules.
- Encryption and Certificates: Employ encryption techniques (as discussed earlier) to secure data in transit. Ensure the use of digital certificates and signatures for authentication and data integrity. Regularly update these certificates to maintain their validity.
- Anti-Virus Software: Keep your anti-virus software up to date. Regular updates ensure protection against the latest threats.
- Network Operating System Updates: Regularly update your network operating system. These updates address vulnerabilities and enhance overall security.
To ensure robust and secure software at a programmer/code level:
- Choose Secure Programming Languages: Opt for programming languages that come with built-in security features and tools. These languages often include mechanisms to detect and prevent common security errors, reducing vulnerabilities from the outset.
- Data Encryption: Utilize recognized encryption techniques for all data stored within your program. Whether it's sensitive user information, passwords, or confidential data, encryption adds a protective layer.
- Access Control and Permissions: Set up administrative rights within your program. Carefully manage access and permission rights for different users. Limit privileges to what is necessary for their roles.
- Minimize External Dependencies: Avoid loading unnecessary Internet services or libraries unless they are essential for your application. Each external dependency introduces potential security risks. Only include what you truly need.
- Thoroughly Test Your Code: Rigorously test your code to identify and fix errors. Specifically focus on known security issues. Vulnerabilities can be exploited if left unaddressed.
- Keep Code Up to Date: Regularly update your codebase in response to new security threats. Stay informed about security patches and best practices.
- User Trust and Internal Threats: Never blindly trust user input. Validate and sanitize all inputs to prevent injection attacks. Remember that threats can come from within an organization. Accidental misuse by users can lead to major problems.