Lesson 7. Network Security
Lesson Objective
- Describe the different types of security measures: Authentication, Encryption, Firewall, MAC address filtering, Network Policies.
- Should also be able to explain how different security measures can be used to protect a network.
Lesson Resources
Lesson Quiz
Lesson Notes
Network Security
Ensuring the security of data on a network is crucial. When networks are compromised, it can lead to various negative consequences:
- Financial Loss: Breaches can result in financial damages, including theft of funds or costly recovery efforts.
- Reputation Damage: A hacked network tarnishes an organization's reputation. Trust from customers, partners, and stakeholders may erode.
- Public Image Issues: News of a security breach spreads quickly. Public perception of the affected entity can suffer.
- Intellectual Property (IP) Theft: Stolen IP, trade secrets, or proprietary information can harm a company's competitive edge.
1. Authentication
Authentication is the process that verifies the identities of individuals, applications, or services before granting them access to digital systems and resources.
Why is authentication important?
- Protecting Systems: Authentication safeguards systems, data, networks, websites, and applications from unauthorized access.
- Individual Privacy: Strong authentication empowers individuals to conduct online business (e.g., banking) with less risk.
2. Encryption
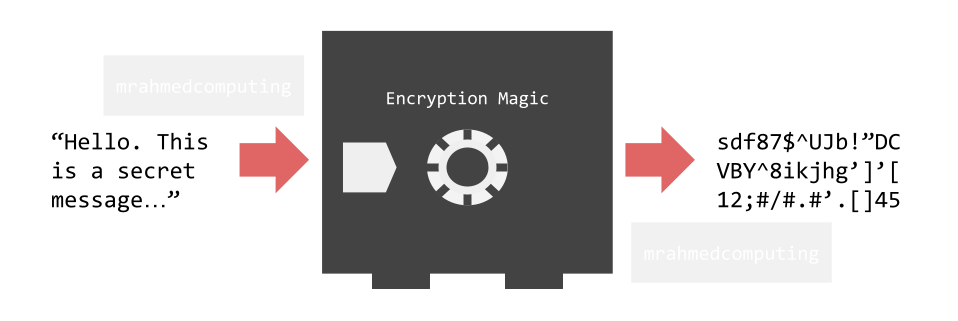
Encryption is the process of scrambling data so that it can not be understood by individuals without appropriate access rights.
Encryption takes plain text (like a text message or email) and scrambles it into unreadable format called ciphertext. This process ensures that even if hackers or cybercriminals intercept the data, they can't read it. The intended recipient, equipped with a decryption key, can unscramble the information back into plain, readable text.
You should encrypt messages, files, and data containing personal, sensitive, or classified information.
3. Firewall
A firewall is like a protective barrier for a network. It allows outgoing traffic but carefully examines incoming traffic. Suspicious packets are blocked, and improper content is rejected. Firewalls also filter unwanted inbound traffic, including blocking specific IP addresses.
4. MAC Address Filtering
MAC address filtering is a network security feature that controls access to a wireless network based on the unique MAC addresses of devices.
Whitelisting (Allowlisting):
- Whitelisting is a security approach that allows only specific, pre-approved items while blocking everything else. This is a very secure choice, however managing and updating the whitelist can be difficult.
Blacklisting (Denylisting):
- Blacklisting is the opposite of Whitelisting and involves creating a list of MAC addresses that are not allowed to access the network. A blacklist can prevent traffic from known entities. As new threats emerge, the blacklist must be continuously updated.
5. Network Policies
Acceptable Use Policy (AUP):
An AUP is an agreement between parties within a computer network community. It outlines standards of behavior regarding the proper usage of specific hardware and software services. AUPs are crucial for minimizing legal risks and ensuring that users adhere to approved behavior.
Disaster Recovery Policy:
This policy prepares an organization for data loss due to disasters such as fire, flood, hardware failure, or hacking. It encompasses evaluating risks, implementing preventive actions, training staff, and executing post-disaster recovery tasks such as procuring replacement hardware, reinstalling software, and restoring data from backups.
Archiving Policy:
Archiving involves storing data no longer in frequent use for security, legal, or historical reasons. Policies define how long data should be retained and how to destroy or delete it after that time. Archiving frees up resources and allows faster access to active data.
Failover Policy:
Failover policies determine how network traffic is rerouted in case of adapter failure. It ensures redundancy by including multiple physical NICs in a team. Failover order specifies which NICs to use when an adapter fails.
Security Policy:
A security policy outlines rules and procedures for network access, authentication, authorization, and encryption. It covers areas like acceptable behavior, incident response, and data protection.