Lesson 1. Cyber Security Threats
Lesson Objective
Define the term cyber security and be able to explain the following cyber security threats:
- Weak and Default Passwords
- Misconfigured Access Rights
- Removable Media
- Outdated Software
- Brute Force Attacks
- DoS
- SQL Injection
- Data Interception
Lesson Notes
Cyber Security Threats
Cybersecurity is the practice of defending computers, servers, mobile devices, electronic systems, networks, and data from malicious attacks. There are also many reasons for why someone would commit a crime usings a computer. Some possible motivations are listed below:
Cybercrime
Cybercrime encompasses any criminal activity that occurs through a computing device.
Hacktivism
Hacktivism refers to hacking a website or computer network with the intention of conveying a social or political message. The person behind such actions is known as a hacktivist.
Cyber Warfare
Cyber warfare involves politically motivated attacks on websites, which may disable them or involve stealing or altering classified data.
Cyber Espionage
Cyber espionage entails using computer networks to gain unauthorized access to confidential information, often held by governments or other organizations.
Threat 1. Weak and Default Passwords
Weak passwords and default passwords pose significant threats to cybersecurity.
Weak Passwords
- Weak passwords are easily guessable because they are too short, simple, or widely used.
- Weak passwords are one of the leading vulnerabilities that lead to data breaches. They provide an open door for attackers to gain unauthorized access to systems, applications, and sensitive information.
- Example: Imagine a Florida water treatment plant that suffered a breach because it was using the same shared TeamViewer password among its employees. These practices can have serious consequences.
Default Passwords
- Device manufacturers and software vendors often use default passwords that are easy to guess. These are the initial passwords set by the manufacturer or developer.
- Attackers can exploit devices or applications with unchanged default settings or stolen passwords. Default credentials are often documented and can be easily found by malicious actors.
Threat 2. Misconfigured Access Rights
Access rights: setting appropriate level of access to members of an organisation.
Misconfigured Access Rights occur when user accounts have incorrect permissions. The bigger problem arising from this misconfiguration is that it can inadvertently grant access to sensitive information to individuals who are lower down the chain of command.
Here is why Misconfigured Access Rights pose a threat:
- Unauthorized Access: When access rights are misconfigured, unauthorized users may gain entry to systems, applications, or data they should not have access to. This can lead to data breaches, privacy violations, and misuse of sensitive information.
- Data Exposure: Misconfigured access permissions can inadvertently expose sensitive data. For example, if a database has overly permissive settings, it might allow unauthorized users to view, modify, or delete critical information.
- Privilege Escalation: Incorrect permissions can enable attackers to escalate their privileges within a system. They might gain administrative access, compromising the entire infrastructure.
- Insider Threats: Even well-intentioned employees can accidentally cause harm due to misconfigured access rights. They might inadvertently delete critical files or expose confidential data.
- Compliance Violations: Organizations must adhere to data protection regulations (such as GDPR, HIPAA, or PCI DSS). Misconfigured access rights can lead to compliance violations and legal consequences.
- Malicious Activities: Attackers can exploit misconfigurations to inject malware, steal sensitive data, or disrupt services. For instance, a misconfigured web server might allow remote code execution.
Threat 3. Removable Media
Removable media (USB Flash Drives, SD Cards, Phones, Cameras, External Drives) poses several security risks that organizations need to be aware of.
- Data Security: When employees copy sensitive data to removable media like USB drives or CDs, there's a risk of unauthorized access. If these devices are lost or stolen, the data they contain could fall into the hands of a person with malacious intent.
- Malware Infections: Removable media can easily carry malware. If an infected device is connected to a network, it can spread malicious software to other systems.
- Copyright Infringement: Unauthorized distribution of copyrighted material can occur through removable media. Employees might transfer sensitive or copyrighted files by mistake.
- Hardware Failures: Removable media can fail, resulting in data loss. If important files are stored solely on these devices, the business could be at risk of disruption as these devices could break easily.
- Insider Threats: Even well-intentioned employees can mishandle removable media.
To mitigate these risks, organizations should:
- Educate Users: Regularly train employees on safe practices regarding removable media.
- Implement Policies: Set clear guidelines for using and managing removable devices.
- Monitor Usage: Keep track of who accesses and copies data to these devices.
- Use Encryption: Encrypt data stored on removable media to protect it even if the device is lost or stolen.
Threat 4. Unpatched and/or Outdated Software
As software becomes older, hackers find flaws and are able exploit them. It is important patch holes when they are found. Here are some points into why this is a security risk:
- Bugs: Over time, software developers discover and fix security vulnerabilities. When software is not updated, these vulnerabilities remain unaddressed. Attackers can exploit them to gain unauthorized access, steal data, or disrupt systems.
- Malware Entry Point: Outdated software becomes an entry point for malware. Worms, viruses, and ransomware often target known vulnerabilities. If your software is not up-to-date, you are essentially leaving the door open for attackers.
To mitigate these threats:
- Keep software up-to-date by applying patches promptly.
- Use tools to automate software updates.
Threat 5. Brute Force Attacks
A brute force attack is a hacking method that relies on trial and error to crack passwords, login credentials, and encryption keys.
In a simple brute force attack, the hacker manually guesses a user's login credentials without using any software. They try standard password combinations or personal identification numbers (PINs).
These attacks exploit weak passwords (like "password123" or "1234") or poor password practices (such as using the same password across multiple websites).
Attackers may also guess passwords based on minimal reconnaissance, like using the victim's favorite sports team name.
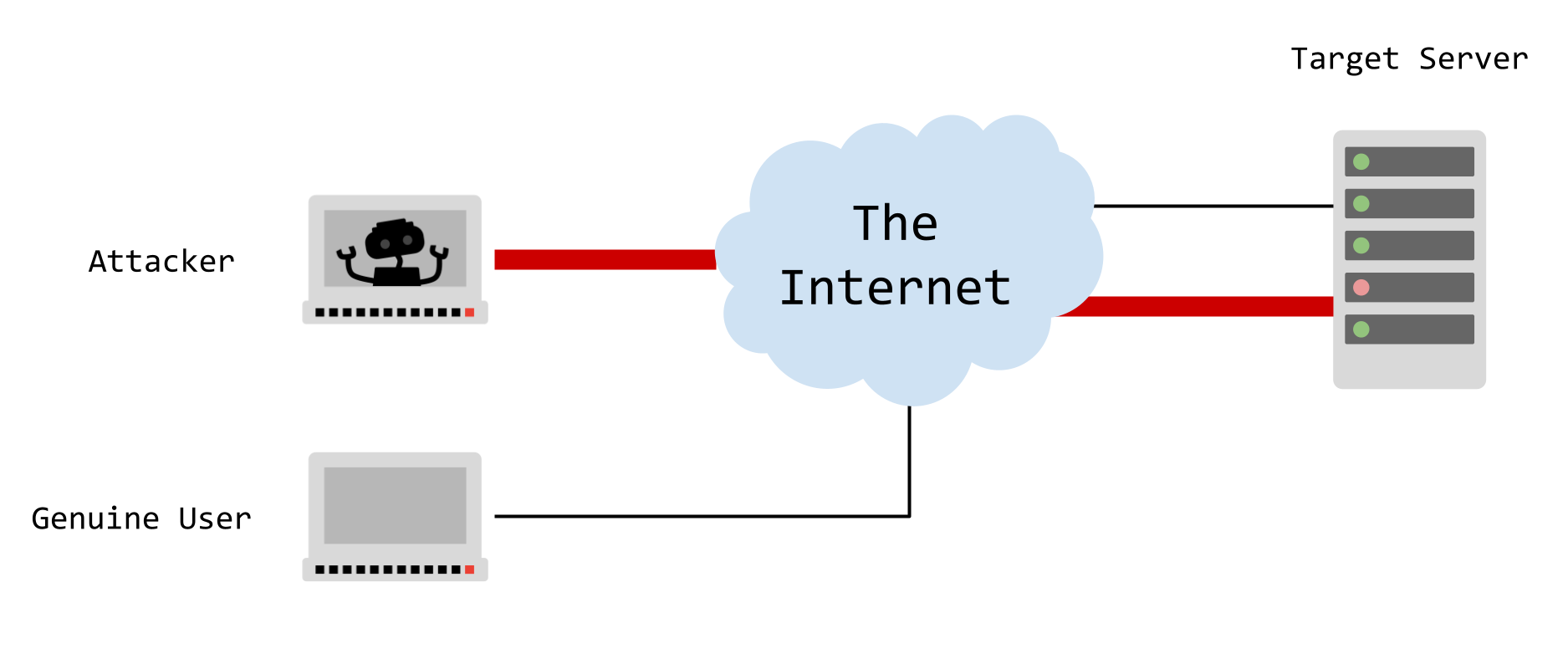
Threat 6. Denial of Service Attack
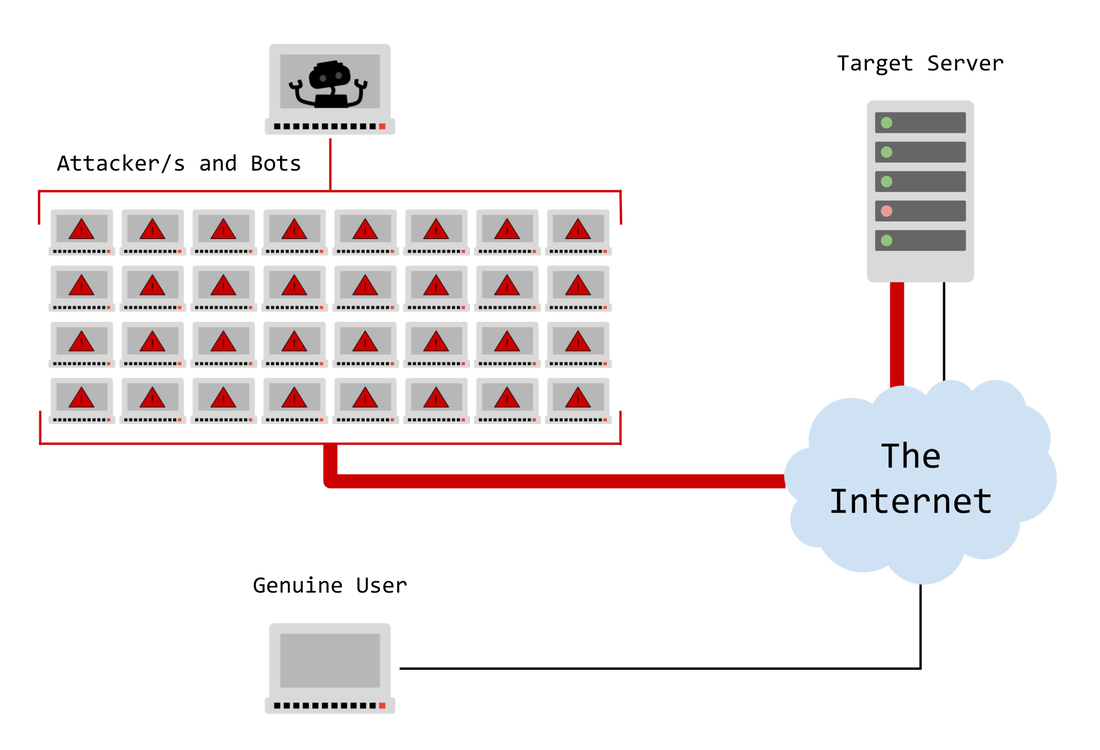
A Denial-of-Service (DoS) attack overwhelms a server with excessive traffic, causing a website or resource to become unavailable. In contrast, a Distributed Denial-of-Service (DDoS) attack is a more powerful variant of DoS, where multiple computers or machines collaborate to flood a specific target.
Denial of Service Attack
Distributed Denial of Service Attack
Here are the key differences:
- Origin:
- DoS Attack: Originates from a single location (a single machine).
- DDoS Attack: Involves multiple remote locations, disguising its origin.
- Speed of Attack:
- DoS Attack: Slower, as it comes from a single location.
- DDoS Attack: Faster, as it comes from multiple locations.
- Traffic Volume:
- DoS Attack: Limited by a single machine.
- DDoS Attack: Employs multiple remote machines (zombies or bots), sending larger amounts of traffic simultaneously.
- Execution:
- DoS Attack: Typically carried out using a script or tool from a single machine.
- DDoS Attack: Coordinates multiple infected hosts (bots) managed by a command-and-control (C&C) server.
- Tracing of Source:
- DoS Attack: Easier to trace back to its origin.
- DDoS Attack: Tracing the actual origin is more complicated due to the use of a botnet.
Threat 7. SQL Injection
SQL injection is a code injection technique commonly used by attackers to exploit vulnerabilities in data-driven applications. In SQL injection, malicious SQL statements are inserted into an entry field (such as a login form) for execution. The attacker crafts input that manipulates the database, potentially revealing sensitive data or causing unintended actions.
Successful SQL injection attacks can lead to data breaches, unauthorized access, and compliance violations.
Example:
Imagine a login form where a user enters their username and password. If the application does not properly validate input, an attacker can input malicious SQL code. For instance, they might input 105 OR 1=1, which would always evaluate to true. The SQL query would then return all rows from the "Users" table, granting unauthorized access.
Threat 8. Data Interception and Theft
Data travels across networks in packets and packets can be intercepted.
Data can be intercepted during wireless transmission. It can be intercepted while traveling over a WAN through telecommunications infastructure. It can also be intercepted physically e.g. portable hard drive being stolen.
This threat could be prevented through the use of encryption.
Threat 9. Poor Network Policies
Network policies are sets of rules and configurations that govern how network devices and systems behave. They define the conditions, constraints, and settings for network communication.
Network policies can also allow you to designate who is able to access a network and how people should use the network.
If non existent or written poorly, then organisations could be put at risk.