Lesson Objective
Understand and be able to explain: Password systems, Biometric measures, CAPTCHA, Email confirmations, Automatic software updates, Physical Security, Encryption, Access Rights, Removable Media bans.
KS3, GCSE, A-Level Computing Resources
Understand and be able to explain: Password systems, Biometric measures, CAPTCHA, Email confirmations, Automatic software updates, Physical Security, Encryption, Access Rights, Removable Media bans.
Organizations may have vulnerabilities in the following areas
Software that is used to detect and remove malware.

Passwords are the most common form of authenticating a user. Authentication is checking that the user is allowed to access content. Some applications use a pin pattern instead of a username and password
To set a secure password you must
Example of strong password: Brdu8#Jw4g
Biometric security is a powerful mechanism that leverages unique biological measurements or physical characteristics to verify an individual's identity and grant access to a facility or system. Unlike traditional passwords, which can be vulnerable, biometrics link proof of identity to our bodies and behavior patterns. Examples of biometric technology include fingerprint mapping, facial recognition, and retina scans.
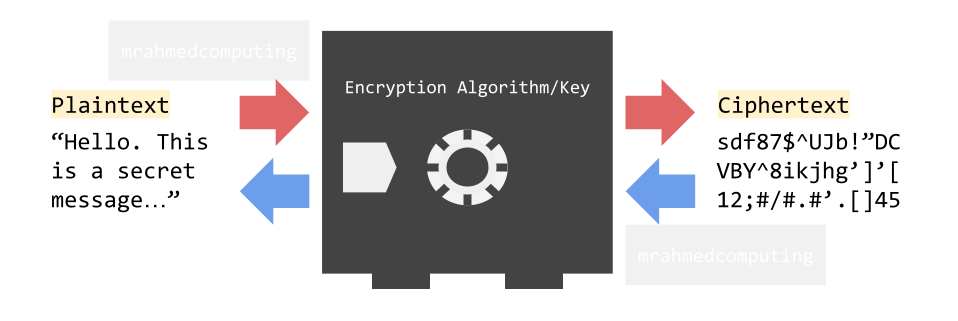
Encryption is the encoding of data so that it can no longer be easily understood. Only authorised users, or users with the key can decrypt it.
CAPTCHA, an acronym for Completely Automated Public Turing test to tell Computers and Humans Apart, serves as a crucial security mechanism. Its purpose is to differentiate between human users and automated bots, particularly in scenarios like signing up for internet services.

Email confirmation serves as a security measure in several ways:
Large companies like Microsoft often automatically update your software whenever they make changes to it. During software installation, you can set the default option to install automatic updates. Free applications typically do not have automatic update capabilities, so manual updates may be necessary. Software patches are updates designed to improve or fix a program. It may also provide additional protection against malware.

Finding flaws in a system, creating a report and explain how to fix them.
Different types testers or hackers can have different motivations and they are categorized into the groups identified below:
Cybercriminals occasionally employ a clever tactic! They strategically "lose" malware-infected USB sticks in places like company parking lots. Their goal is to trick unsuspecting employees into picking up these USB drives and plugging them into their computers. Thankfully, in some cases, vigilant employees have thwarted these attempts by reporting the suspicious devices to their IT departments. It's a reminder to stay cautious when encountering stray USB drives!
Access rights in network security refer to the permissions and privileges granted to users, devices, or processes within a networked environment. These rights determine what actions an entity can perform and what resources it can access.
Set of rules to follow in an organisation. If the rules are broken the organisation has legal grounds to remove you.

Physical security is used to prevent physical access to devices, and to prevent theft. Steps may include: